India Stood at fifth Position, in the Global Data Breach Rankings
In 2023, India ranked fifth globally in terms of the highest number of account breaches, with 5.3 million accounts exposed. Worldwide, a staggering Rs 30 crore was crossed, with the U.S. topped the list with data breach of 34%, followed by Russia, France, and Spain in second, third, and fourth. It has moved up to fifth in time.
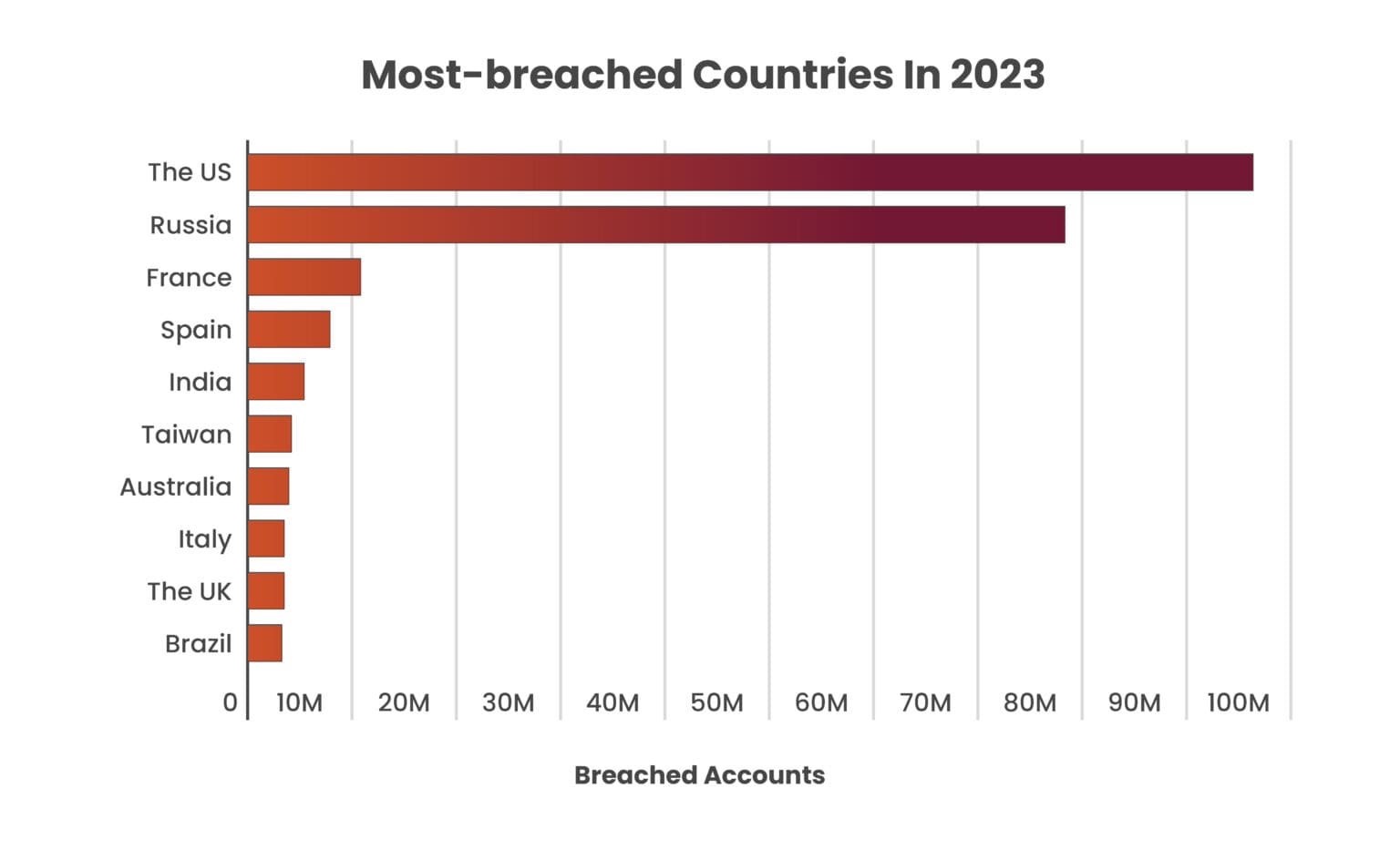
The study highlights the serious risk that data breaches provide to the safety of net clients. This information was gathered from Surfshark’s report of 29,000 publicly available databases. More often than not, hackers breach data by sending spam emails and can distribute viruses to computers. In this blog, we will discuss data breach issues and how organizations can prevent such breaches.
How Hathway was Hacked by Hackers?
Hathaway experienced a fact breach in December 2023 that revealed 41.Data on five million customers, including names, email addresses, phone numbers, and physical addresses. Establishing the significance of robust safeguards and systems required to stop such intrusions is crucial. Because the breach led to the use, disclosure, or destruction of private information without authorization in addition to a breach of the record’s confidentiality. When it was discovered that the stolen records had been bought for $10,000, concerns regarding the improper handling of sensitive personal data increased.
What Happened at Air India?
Hackers attacked Air India’s database, gaining unauthorized access to the personal details of 4.5 million of its customers. This breach occurred shortly after a similar incident at Akasa Air. Following the breach, Air India notified affected passengers via email, acknowledging that their data security had been compromised. The stolen information included user IDs and passwords.
The hackers managed to acquire sensitive data, enabling them to access passengers’ GST invoices and subsequently disclose them publicly. However, Air India refuted allegations that credit card details such as CVC and CVV numbers were compromised, asserting that they remained secure.
Data Breach Incident at Upstox
Hackers gained access to the KYC and other personal data of 2.5 million clients by breaking into the security systems of Upstox, the second-largest stockbroking company in India based on purchaser numbers. A report aided by the Times of India found that the pilfered data was linked to a third-party storage facility before being posted to the shadowy internet.
The breach has been attributed to a group known as ‘Shiny Hunters’, according to investigators. It was found that the hackers managed to obtain access to account information by acquiring the Amazon Web Service Key.
How These Incidents Can Be Prevented?
Businesses need to be proactive in reducing the risk of cyberattacks. Credit card facts are protected by making sure the charge card enterprise (PCI) is licensed and complies with its safety requirements. Particularly for mobile devices, encrypting WiFi networks and using strong passwords can help prevent unwanted access.
Best Practices for Cybersecurity
Establish a Robust Cybersecurity Policy
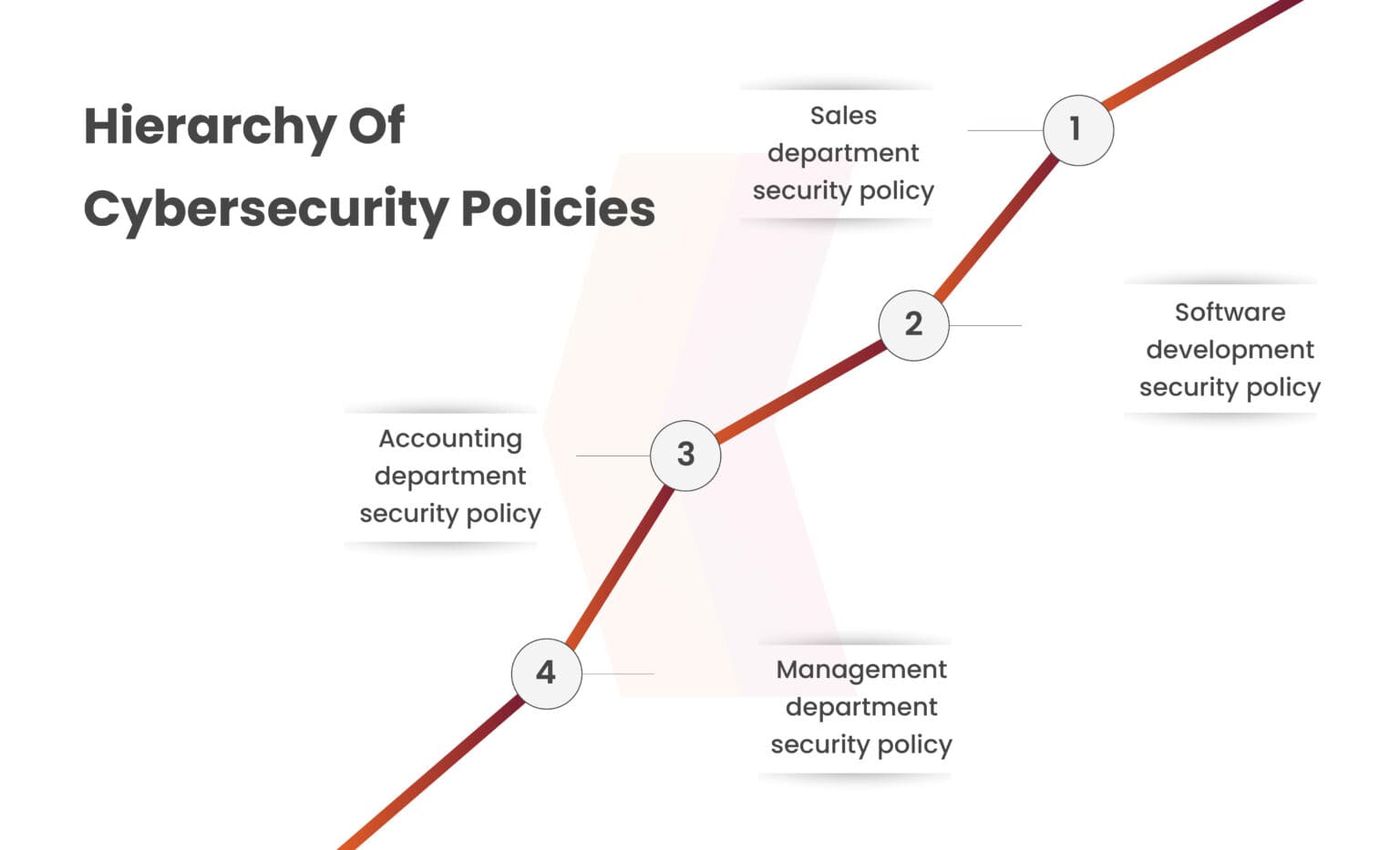
A cybersecurity policy acts as a formal framework outlining the cybersecurity measures employed by your company to enhance security effectiveness. It ensures alignment between security specialists and employees by detailing essential information security practices that apply company-wide. Adopting a hierarchical approach to cybersecurity policy implementation involves having a centralized policy supplemented by department-specific policies tailored to address the unique needs of each department. This approach enhances overall cybersecurity policy effectiveness while minimizing disruptions to departmental workflows.
Secure Organization’s Perimeter and IoT Connections
Because of the widespread use of remote work, cloud environments, and IoT devices, organizational access goes far beyond traditional firewalls and DMZs, significantly broadening the attack surface. The Internet of Things market is expected to reach $567 billion by 2027 if it continues to expand. With connected security cameras, doorbells, smart locks, and other types of IoT devices, potential attacks are established. For instance, a compromised printer could grant access to sensitive documents. To bolster perimeter security, safeguard border routers, and establish screened subnets. Additionally, it enhances database security by isolating sensitive data from the corporate network and enforcing access restrictions. Enhance traditional security measures such as firewalls and VPNs with a zero trust model, which mandates continuous trust of users and devices to prevent unauthorized access as opposed to “do not accept.” never have, always prove” principle fits.
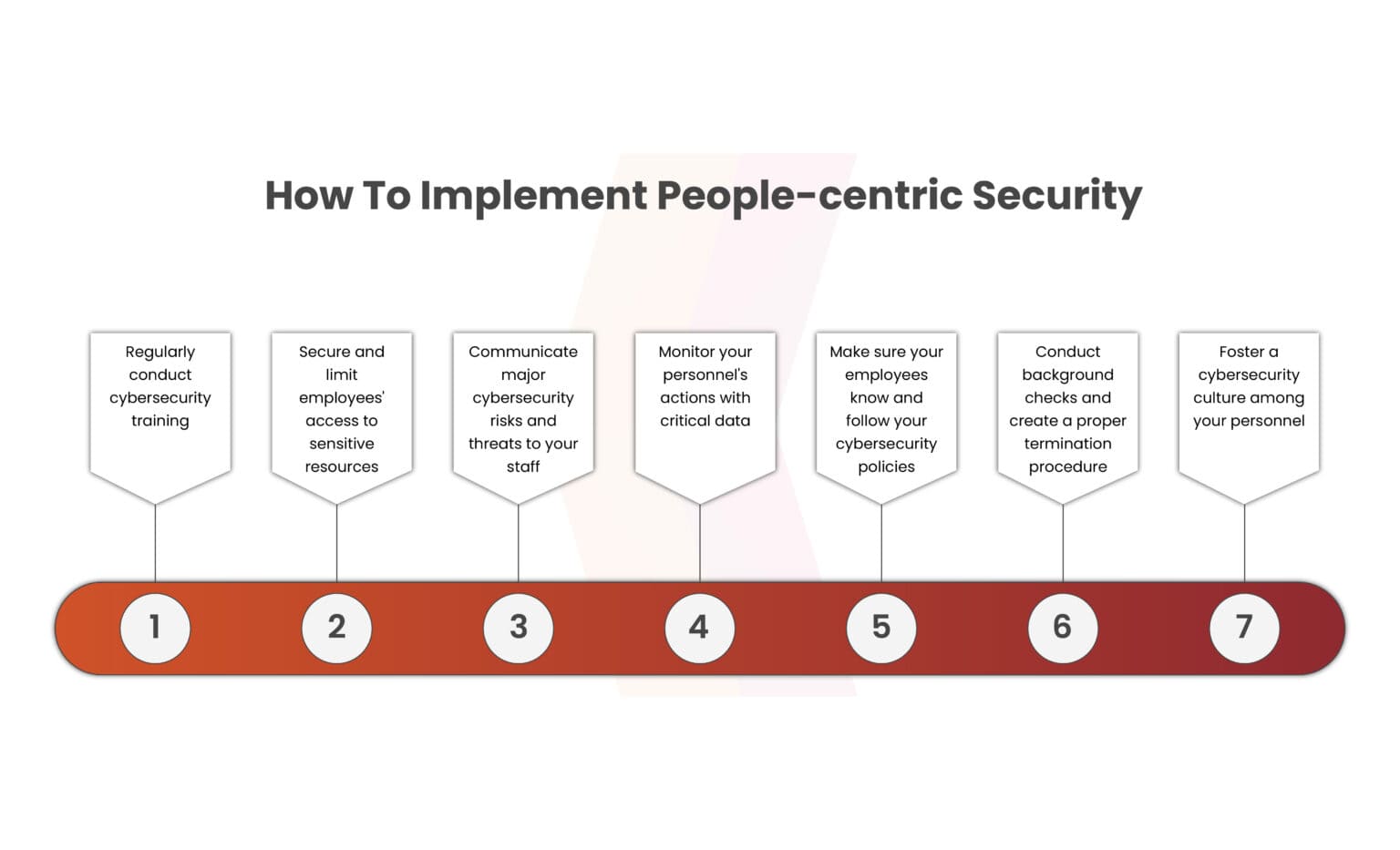
Implementation of People-Centric Policy
In this approach, employees themselves form a critical perimeter. Educating and monitoring staff are key aspects of establishing a secure people-centric environment. To transition your organization’s cybersecurity to a people-centric model, contemplate the following steps:
Control Access to Sensitive Data
Providing employees with excessive privileges by default poses a risk by granting access to sensitive data unnecessarily. This approach heightens the threat of insider attacks and enables hackers to compromise data when an employee’s account is breached.
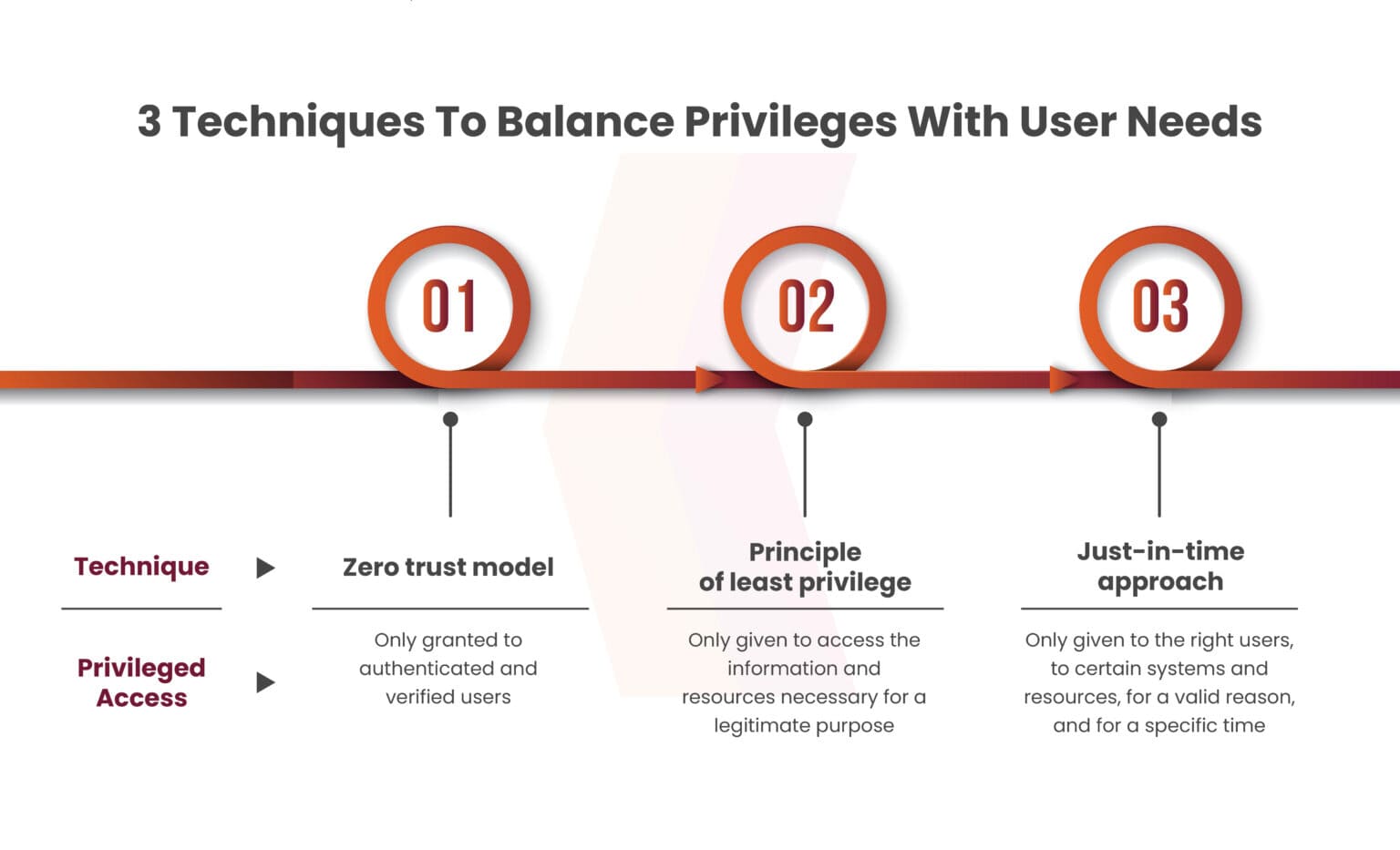
Implementing the least privilege model, also known as the principle of least privilege, offers a more effective solution. This entails assigning each user the minimum access rights required and elevating privileges only when necessary. If access to sensitive data is not required, corresponding privileges should be removed.
Additionally, adopting a just-in-time access management approach adds further granularity to controlling user privileges. This involves granting access to employees upon request for a specific duration and with a valid reason. Organizations can enhance their access management practices by combining these techniques.
Conclusion
The number of information breaches worldwide has increased significantly in 2023, with India coming in fifth place. These hacks brought to light how urgently stronger cybersecurity laws across all sectors are needed. The events at Hathaway, Air India, and Upstox provide a reminder that businesses need to give cybersecurity top priority in order to safeguard sensitive data and preserve customer trust. Organizations can improve their cybersecurity posture by using quality practices along with strong cybersecurity policies, securing IoT networks and organizational reach. This can be done by managing access rights to critical data, handling supply chain risks through C-SCRM, and managing information breach risks.